Secure SDLC Process
Overview
The Secure Software Development Lifecycle (SDLC) integrates security at every phase of the software development process. This ensures that security is considered from the inception of the project through to deployment and maintenance. By embedding security practices throughout the SDLC, we can identify and mitigate vulnerabilities early, reduce risks, and deliver robust, secure software products. Below explains the Secure SDLC process that PenfieldAI follows.
Key Phases in Secure SDLC
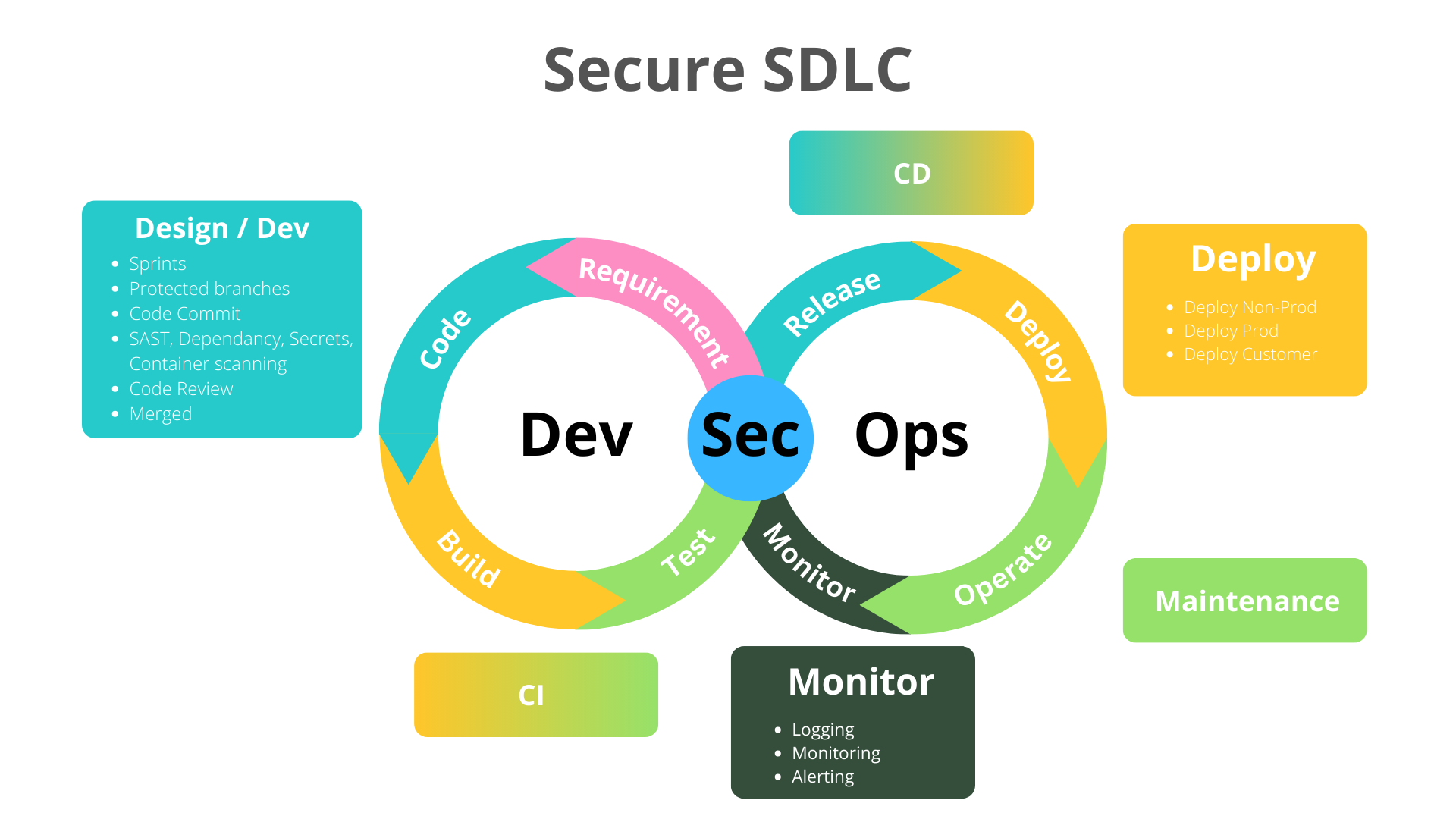
1. Requirement
- Requirement Gathering: Collect and document functional and security requirements from stakeholders.
- Feedback Analysis: Review and analyze feedback to refine requirements and ensure they address potential security concerns.
- Threat Modeling: Conduct threat modeling exercises to identify and mitigate potential security threats early in the development process.
- Privacy Considerations: Ensure that privacy considerations are addressed in the requirements.
2. Design/Development
- Review and Planning: Conduct security reviews during planning to identify potential threats and design security controls.
- Sprints: Implement security best practices in each sprint, ensuring that security is part of the development process.
- GitLab Flow Best Practices: Follow GitLab Flow best practices, such as maintaining a clean and organized branch structure.
- Protected Branches/Tags: Use protected branches and tags to prevent unauthorized changes.
- Vulnerability Scanning (SAST, DAST): Conduct static application security testing (SAST) , dynamic application security testing (DAST), and dependency scans in the automated pipeline to catch vulnerabilities both in code and runtime..
- Approval Rules: Establish approval rules for code merges based on security assessments.
- Code Review: Perform rigorous code reviews with a focus on identifying security issues.
- Code Merged: Ensure that only code meeting security standards is merged into the main branch.
3. Continuous Integration (CI)
- Automated Builds: Implement automated build processes that include security checks.
- Test: Run automated tests, including security tests, to validate code changes.
4. Security
- Container Scanning: Scan container images for vulnerabilities before deployment.
- Dependency Scanning: Scan dependencies for known vulnerabilities.
- Merge Request Security Scan Results: Review security scan results for each merge request.
- Security Approval Gate: Implement security approval gates to ensure that security checks are passed before proceeding.
- Project Security Dashboard: Maintain a project security dashboard to track and monitor security metrics.
5. Continuous Deployment (CD)
- Deploy Non-Production: Deploy to non-production environments and perform dynamic application security testing (DAST).
- Create Release Tags: Create release tags for version control and traceability.
- Verify Checklist: Verify that all release checklist requirements are met before production deployment.
- Prod Deploy: Deploy to production with confidence, knowing that security and change has been validated.
- Customer Deploy: Deploy or send updates to customers, ensuring they receive secure software.
6. Monitor/Maintenance
- Grafana (Dashboard): Use Grafana for monitoring and visualizing application performance and security metrics.
- Prometheus (Monitoring): Implement Prometheus for real-time monitoring and alerting.
- Loki (Logging): Use Loki for centralized logging and quick identification of security issues.
- Alert Manager: Configure alert managers to notify teams of security incidents.
- Teams/PagerDuty: Use communication tools like Teams or PagerDuty for incident response and management.
General Secure SDLC Practices:
Apart from above mentioned key phases, following are some general practices that Penfield.ai follows to ensure secure SDLC process:
- Secure Coding Practices: Educate and enforce secure coding practices among developers to prevent common vulnerabilities.
- Penetration Testing: Annually perform penetration testing to identify and fix vulnerabilities in the application.
- Security Training: Provide ongoing security training and awareness programs for development and operations teams.
- Compliance and Standards: Ensure compliance with relevant security standards and regulations.
Conclusion
Implementing a Secure SDLC ensures that security is an integral part of the software development process, leading to more secure and reliable software products. By following the structured process outlined above, we can deliver software that meets both functional and security requirements, providing our customers with the assurance that their data and systems are protected.