PenfieldAI and Microsoft Sentinel integration
In order to pull incident data from Microsoft Sentinel, sentinel integration need to be setup with penfield product. This document provide the detailed view of the integration setup.
Microsoft Sentinel account setup
Click on New Registration
-
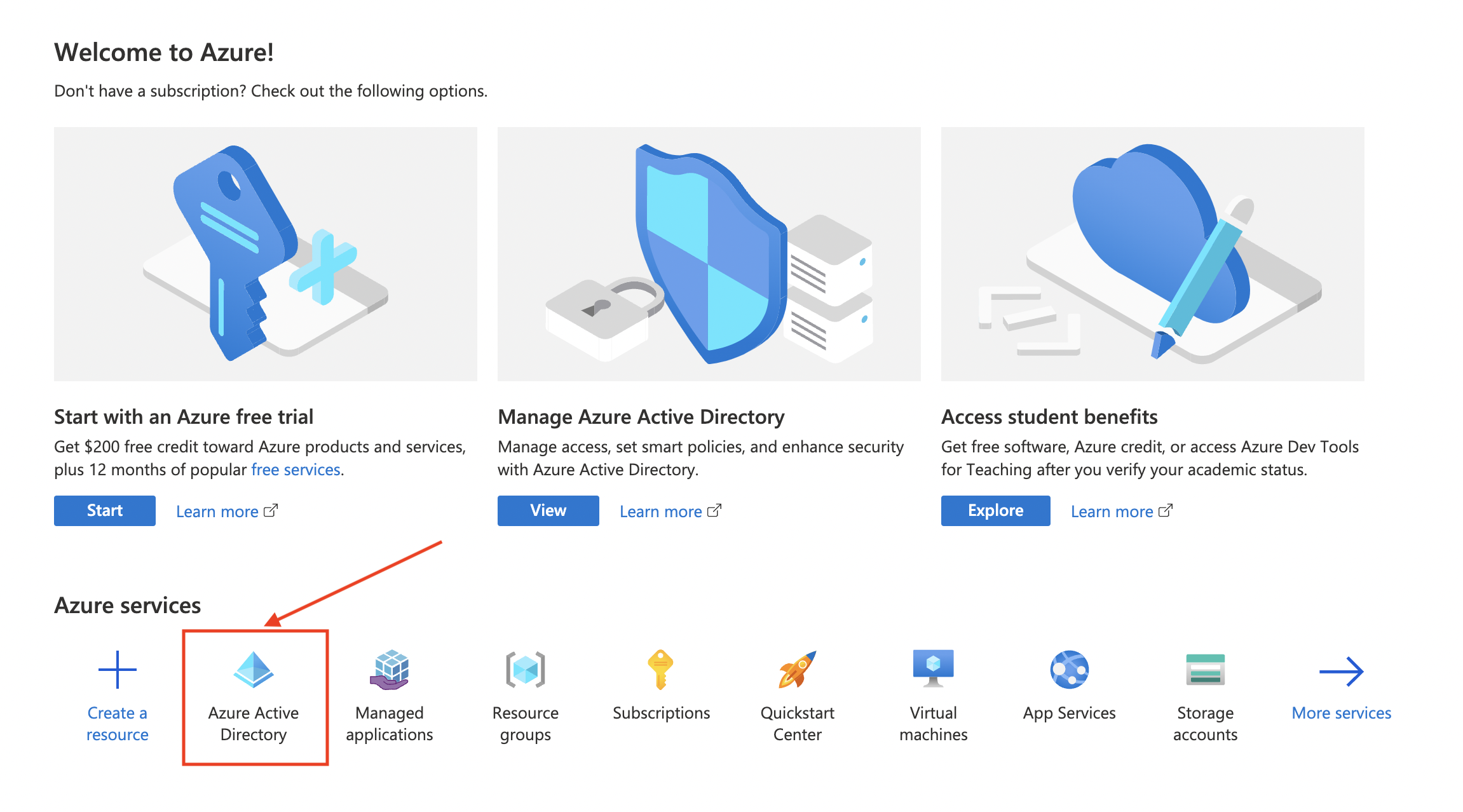
Login to https://portal.azure.com/#home
-
Navigate to Azure Active Directory
-
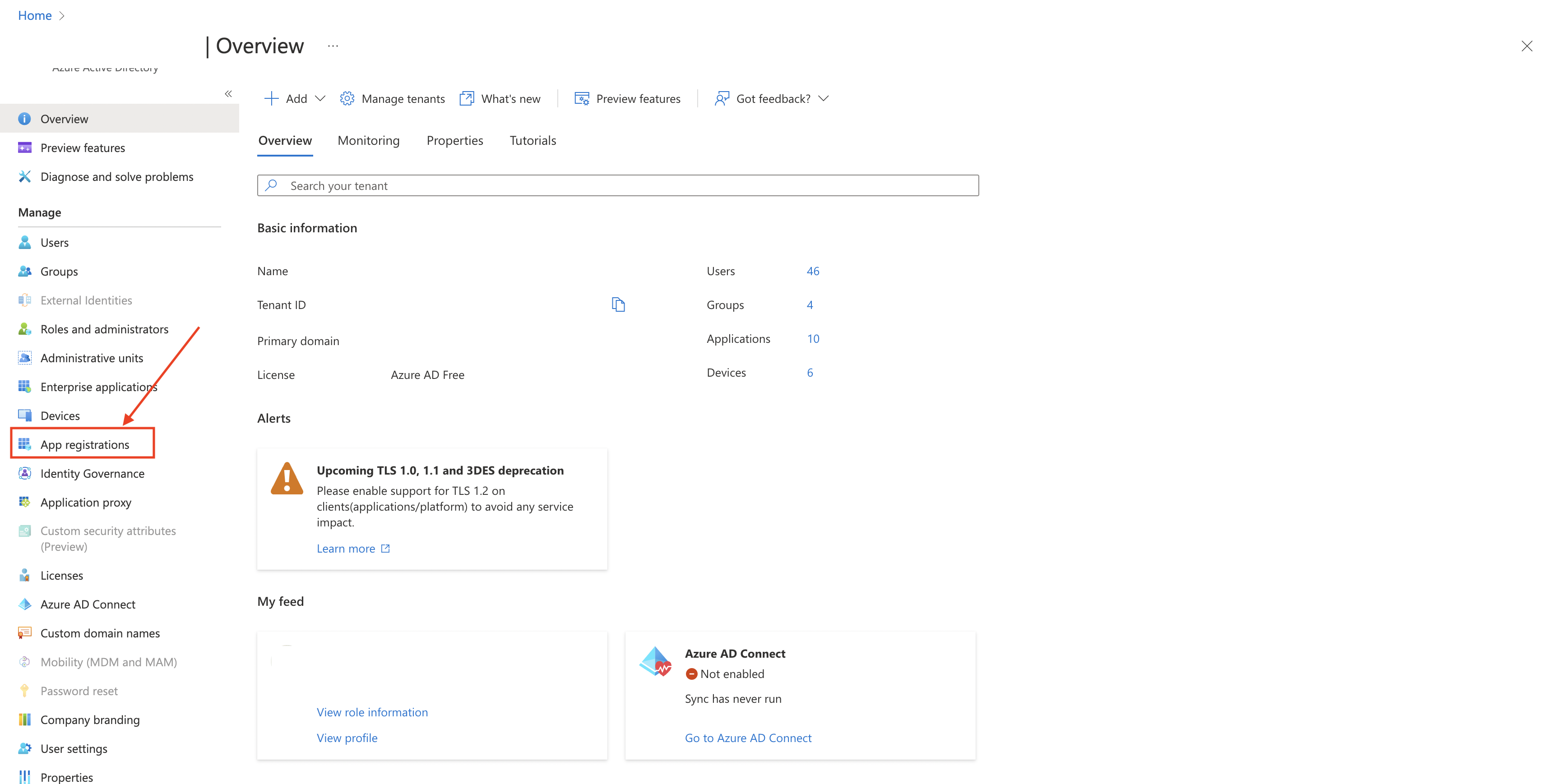
Navigate to App Registration
-
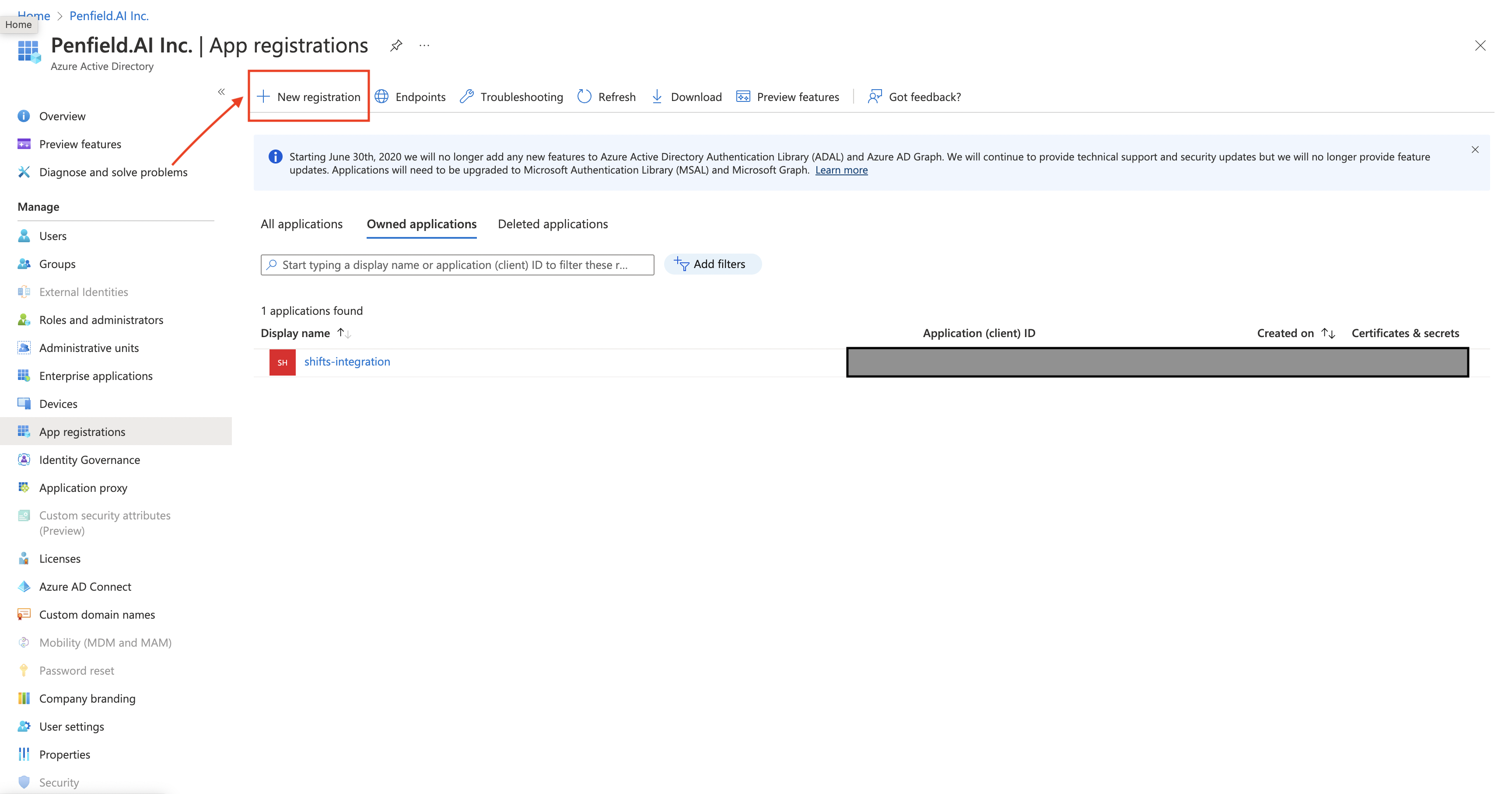
Click on New Registration
-
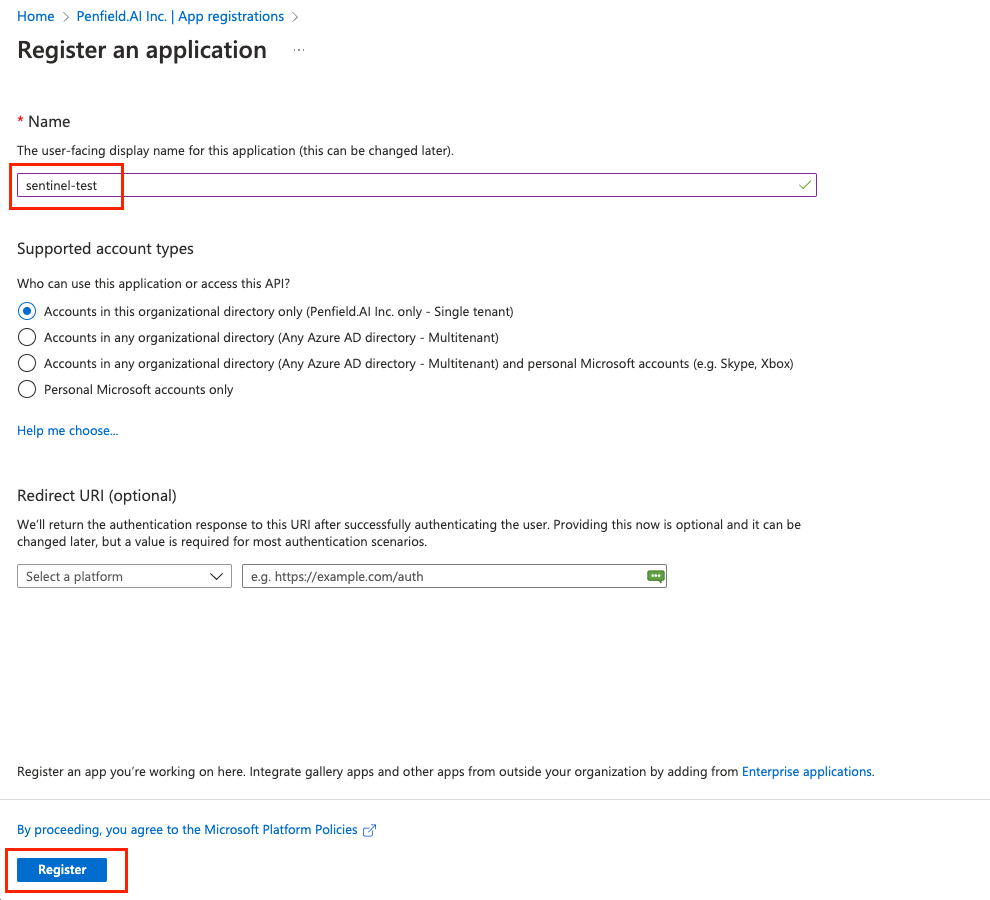
Please fill out the form and then click on Register. Please fill out the form with the following values
- Choose appropriate Name as required
- Under Supported account types, select the
Accounts in this organizational directory only (<Company Name> only - Single tenant)option. - Redirect URI is not needed.
-
Copy the Application (client) ID and the Directory (tenant) ID
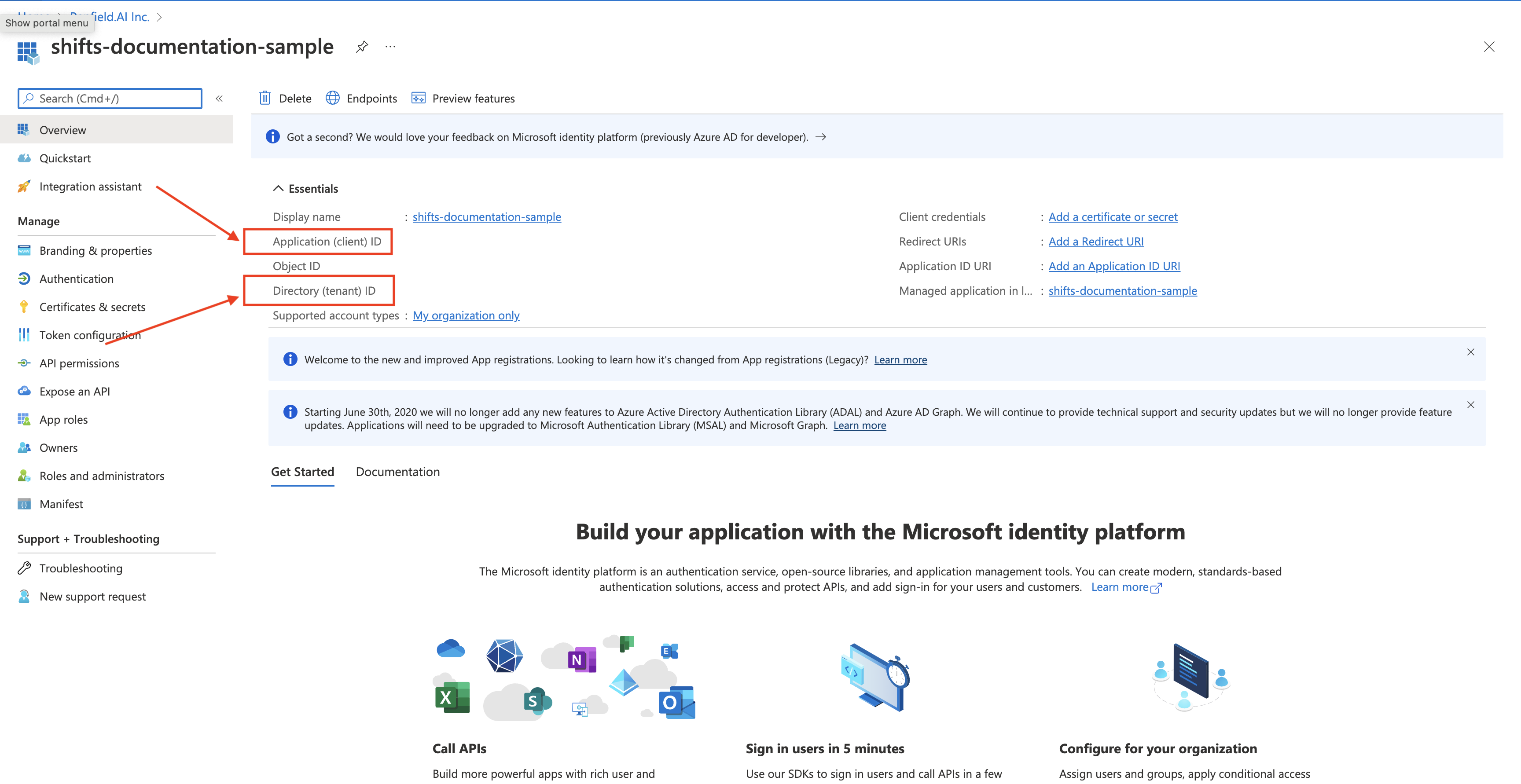
-
Navigate to Certificates & Secret, then click on New client secret
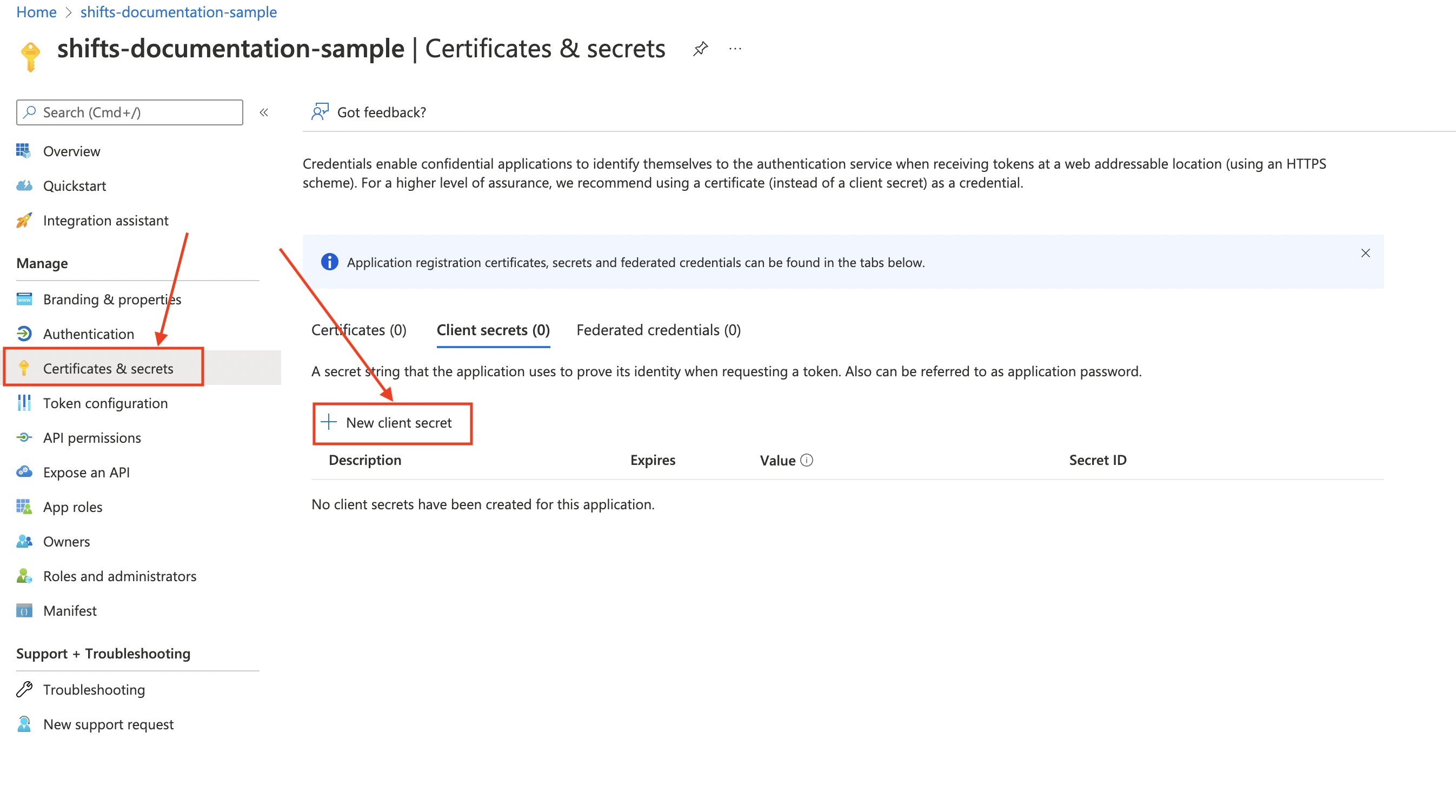
-
Fill in the details for the fields in the form that is shown in the side panel. Click Add
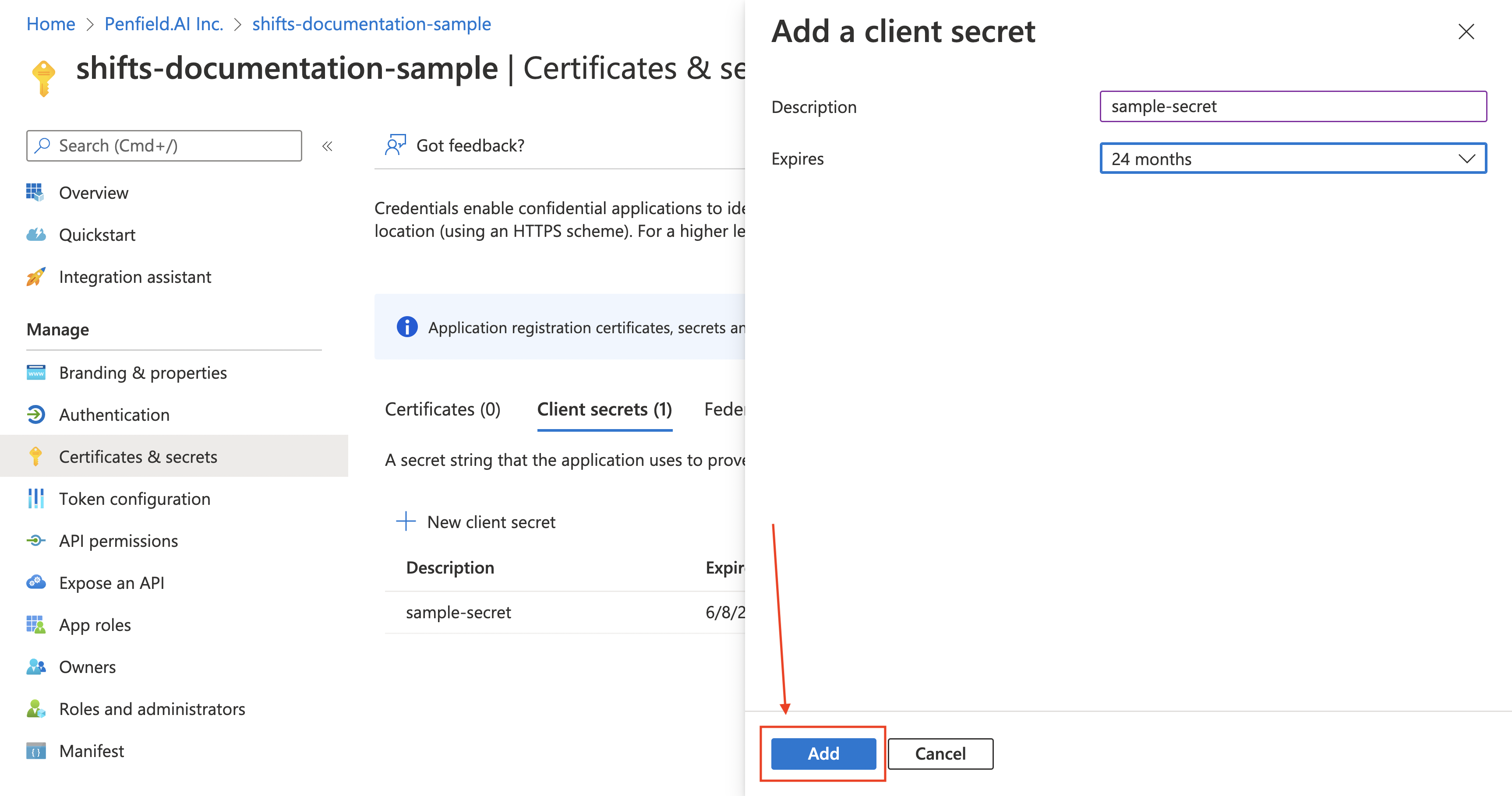
-
Copy the secret value
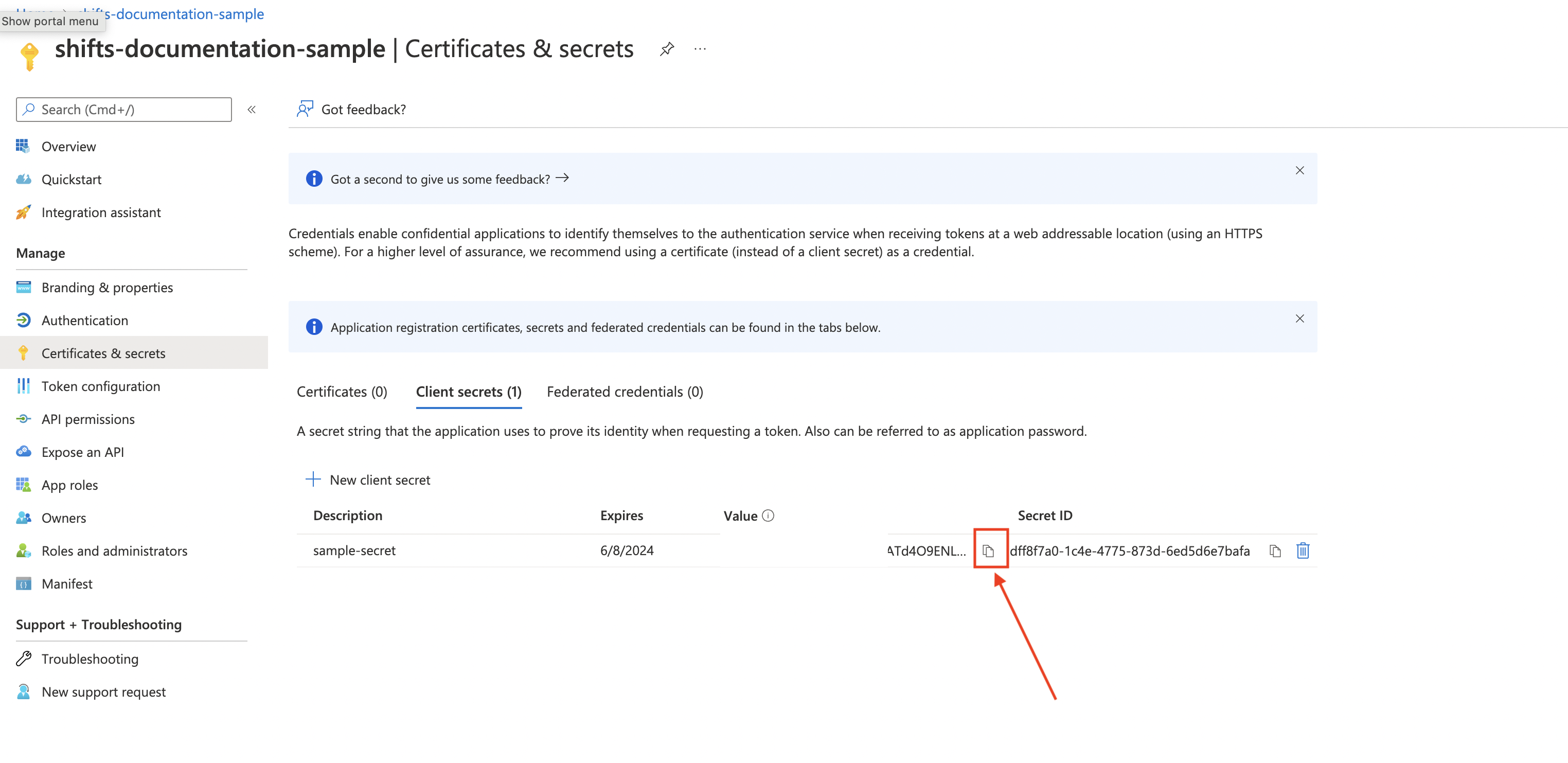
-
Assign a role to the registered app.
- In the Azure portal, Go to Subscriptions, select the subscription in which sentinel is setup → Access control (IAM)
- Click Add >> Add role Assignment

- Select the Microsoft Sentinel Responder role , Go to Members.
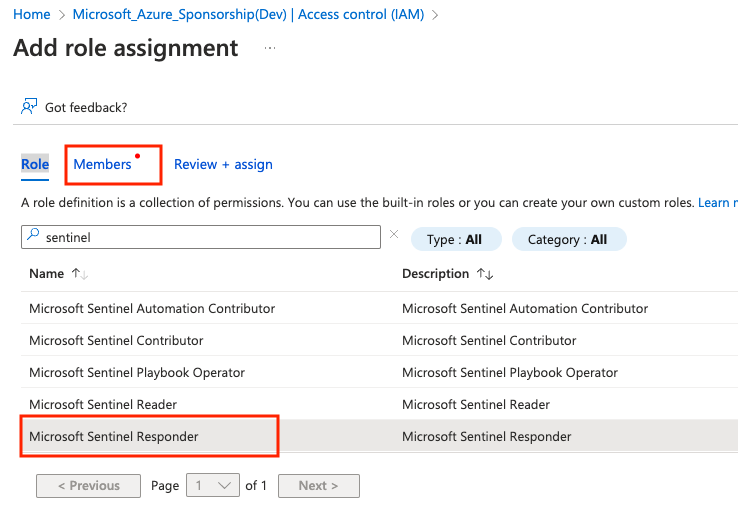
- In the Assign access to choose User, group, or service principal and in the members on the right choose the app that was created previously in step 5 and click Review+ assign.
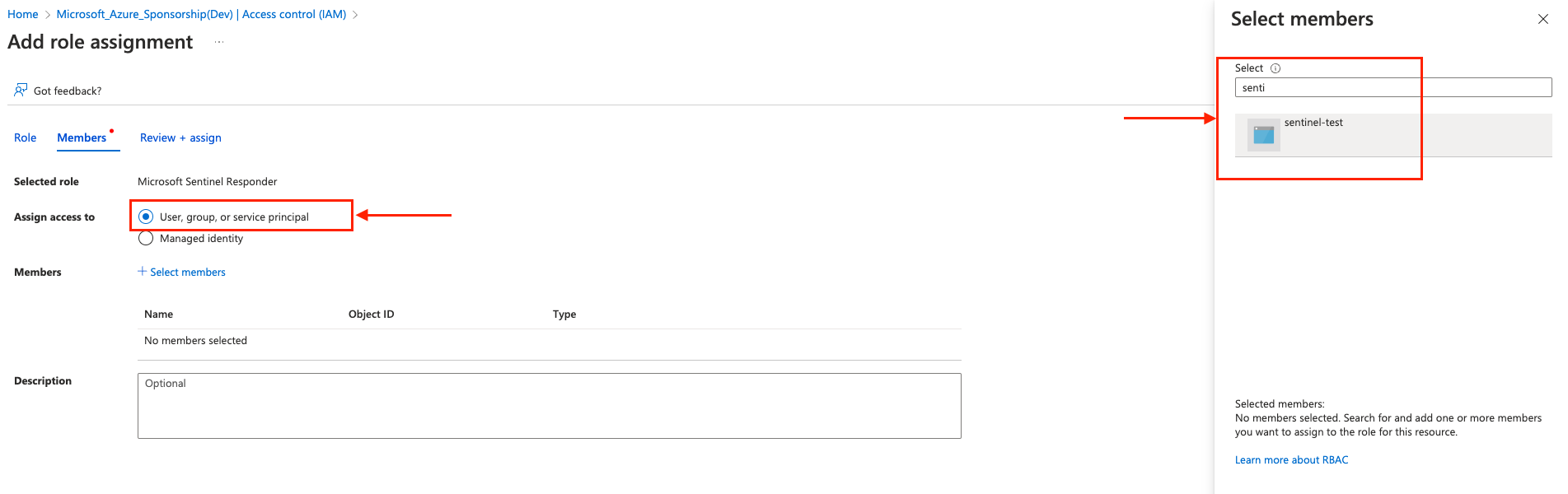
-
At this step account setup is completed. Please note down following values:
Here is the list of values that will be needed:
- tenantID - Directory (tenant) ID (Step 6)
- clientID - Application (client) ID (Step 6)
- clientSecret - Step 9
- azure subscription ID where sentinel is setup
- sentinel workspace name
- sentinel resource group name
If you are deploying penfield.ai product as a self-service please proceed with next steps, otherwise send these values to Penfield team secure means like onetimesecret or other secret management tool you use.
Update Penfield app configuration
-
Update penfield-app secrets, with secret
SENTINEL_INSTANCES. String value is constructed in this format, replaceVALUEfrom the above values accordingly in the below string and then encode into base64.[{"name": "VALUE(name corresponds to your organization)", "subscription_id": "VALUE", "workspace_name": "VALUE","resource_group_name": "VALUE", "tenant_id": "VALUE", "client_id": "VALUE", "client_secret": "VALUE"}]- if you have multiple sentinel instances in different subscriptions, you need to do sentinal account setup in each of the subscription (follow all the above 11 steps for each account) and secret
SENTINEL_INSTANCESvalue will be like:[{"name": "VALUE1(name corresponds to your organization)", "subscription_id": "VALUE1", "workspace_name": "VALUE1","resource_group_name": "VALUE1", "tenant_id": "VALUE1", "client_id": "VALUE1", "client_secret": "VALUE1"},{"name": "VALUE2(name corresponds to your organization)", "subscription_id": "VALUE2", "workspace_name": "VALUE2","resource_group_name": "VALUE2", "tenant_id": "VALUE2", "client_id": "VALUE2", "client_secret": "VALUE2"}]
- if you have multiple sentinel instances in different subscriptions, you need to do sentinal account setup in each of the subscription (follow all the above 11 steps for each account) and secret
-
Once secrets are updated, sentinel integration needs to be enabled in the helm charts values file penfieldai-values-[tier].yaml, Append these values shown in follwoing snippet in your values file.
# Replace {subscription_id}, {resource_group_name}, {workspace_name} as per above values.
configs:
SENTINEL_BASE_REQUEST_URL: "https://management.azure.com/subscriptions/{subscription_id}/resourceGroups/{resource_group_name}/providers/Microsoft.OperationalInsights/workspaces/{workspace_name}/providers/Microsoft.SecurityInsights/"
#Services:
sentinel-inbound-integration:
enabled: true
incidentsPull:
enabled: true
image:
registry: ""
repository: penfieldai/sentinel-inbound-integration/incidents-pull
tag: ""
processing:
enabled: true
image:
registry: ""
repository: penfieldai/sentinel-inbound-integration/processing
tag: ""